 From time in memorial, people have used cryptography to scramble messages to maintain their confidentiality. At the origin, the message is scrambled and at the destination it is descrambled as per a prearranged logic.
From time in memorial, people have used cryptography to scramble messages to maintain their confidentiality. At the origin, the message is scrambled and at the destination it is descrambled as per a prearranged logic.
To understand data encryption, let us look at an example. If you want to send the message: ‘hello world’ on the Internet you may encrypt it by replacing each letter by the next letter so ‘h’ becomes ‘i’; ‘e’ becomes ‘f’ and so on. As per this scheme, the encrypted message is ‘Ifmmp Xpseme’. At the receiving end, this message is decrypted by replacing the letter by the previous letter to obtain the original message.
There are four elements to the encryption system:
- The plain text – the message to be encrypted. In our example, it is ‘hello, World’.
- The key-that is the string or digits. In our example it is “1”
- The ciphertext is the encrypted message. In our example it is ‘Ifmmp Xpsme’.
- Cryptographic algorithm – this is the logic to combine the plain text with the key to generate the ‘ciphertext’. It is also used to convert the ciphertext to plain text using the key. In our example, the cryptographic algorithm for encryption is ‘replace each letter by the letter that succeeds it by the number represented by the key’. The logic for decryption is reverse of this.
As per this scheme if the key was ‘2’, the ciphertext would have been ‘Jgnnq Yqtnf’.
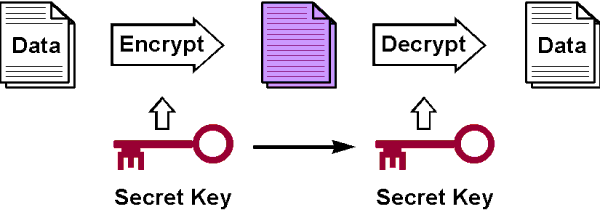
There are two common type of encryptions in use today; secret-key and public-key encryption.
Contact us for Free web Design Demo